
Scam callers are a growing problem that can result in financial loss and identity theft. Here are some key points to keep in mind when dealing with scam callers:
Scammers use a variety of tactics: Scammers use false promises, aggressive sales pitches, and phony threats to pry loose information they can use to steal your money or identity.
- They may also use personalized audio messages to simulate an actual personal phone call.
- Scammers target vulnerable populations: Scammers often target vulnerable populations, such as the elderly or those with limited English proficiency.
- Scammers use a variety of payment methods: Scammers use a variety of payment methods, such as wire transfers or gift cards, to make it difficult to recover lost funds.
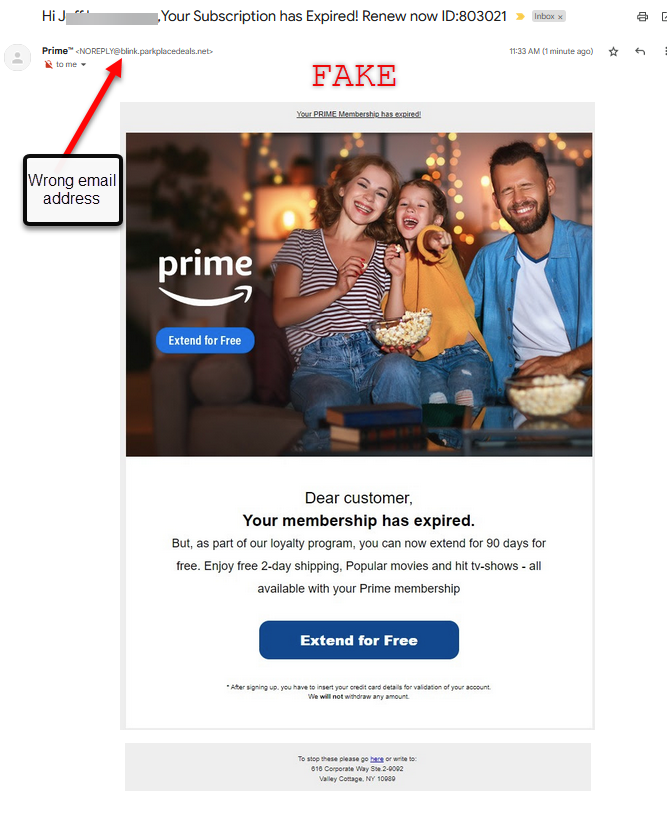
- Scammers often pose as representatives of government agencies: Scam callers often pose as representatives of government agencies or well-known companies to increase the chances that you'll answer.
- Scammers use phishing tactics: Scammers use email or text messages to try to steal your passwords, account numbers, or Social Security numbers.
They may also use spoofing tools to trick your caller ID into displaying a genuine government or corporate number.
To avoid falling victim to scam callers, it's important to be aware of these tactics and take steps to protect yourself. Here are some tips to keep in mind:
- Don't give out personal information: Don't give out personal information, such as your Social Security number or bank account information, to anyone who calls you.
- Hang up: If you receive a call from a scammer, hang up immediately.
- Don't press any numbers: If you receive a robocall, don't press any numbers. Instead of letting you speak to a live operator or remove you from their call list, it might lead to more robocalls.
- Use call-blocking technology: Use call-blocking technology to block unwanted calls.
- Report scam calls: Report scam calls to the Federal Communications Commission (FCC) Consumer Complaint Center.
The data collected helps track trends and supports enforcement investigations.
By being aware of these tactics and taking steps to protect yourself, you can avoid falling victim to scam callers and protect your financial and personal information.

 Scam callers are a growing problem that can result in financial loss and identity theft. Here are some key points to keep in mind when dealing with scam callers:
Scam callers are a growing problem that can result in financial loss and identity theft. Here are some key points to keep in mind when dealing with scam callers: